Product Cybersecurity Vulnerability Management Process
Moxa’s product cybersecurity vulnerability management process encompasses the five stages detailed below. Each stage involves processes and practices that Moxa carefully follows.
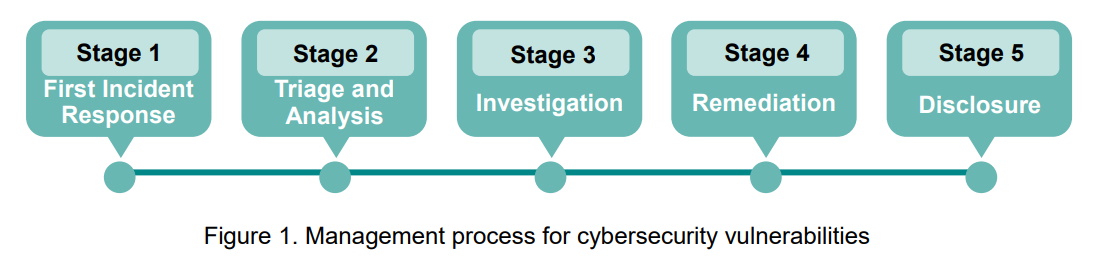
- First Incident Response: As soon as PSIRT receives an external vulnerability report regarding a Moxa product, we will send an initial response within two working days.
- Triage and Analysis: PSIRT triages and analyzes the possible cybersecurity vulnerability and assesses its impact on Moxa products. We will provide a preliminary assessment report at the end of this stage to the person who reported the vulnerability.
- Investigation: PSIRT works closely with the product development team to identify the root cause of the vulnerability and the degree, as well as the extent, of its impact on Moxa products. Next, PSIRT offers solutions to mitigate and solve the issue. During this stage, PSIRT continues to communicate with the person who reported the incident.
- Remediation: PSIRT works closely with the product development team to develop the final software/firmware patches or to finalize the mitigation measures. Meanwhile, PSIRT continues to follow any updates regarding relevant vulnerabilities to assess their potential impact. If the vulnerability poses a high risk for customers, and the development of the final patch takes longer than the customer can wait, Moxa will provide temporary mitigation measures before the final patch becomes available.
- Disclosure: PSIRT will publish the results of the product cybersecurity vulnerability on the Security Advisory section of our website. The report will include a description of any vulnerabilities, the products and versions that are affected, mitigation measures, and remediation plans where appropriate.
Moxa’s PSIRT and development team leverages the Common Vulnerability Scoring System (CVSS) and Moxa’s Risk-based Vulnerability Management Model to assess the potential risks of an incident. PSIRT will create a timeline to address the issue based on several factors: the security context, the possibility of vulnerabilities being exploited, possible impacts, and other factors.
After analyzing the reported vulnerability, Moxa will immediately set up a designated testing environment to determine the severity of the vulnerability. When appropriate, Moxa will continue to communicate with the person who reported the issue. After identifying the root cause and possible severity of the impact, Moxa will proceed to remediation analysis and offer solutions or mitigation measures.
Our security advisory updates and announcements can be found on the Security Advisories section of Moxa’s website and anyone can subscribe to the Security Advisories RSS Feed. If you would like to receive the latest security announcements for specific Moxa products, you have to create an account on Moxa’s website first, before clicking the ‘Follow Updates’ option.