Industrial Control Systems Are Under Attack
Gone are the days of critical infrastructure and industrial networks operating in isolated "islands of automation". Today, nearly every critical network or manufacturing environment is exposed to cybersecurity risks as interconnectivity between IT and OT networks increases. In August 2018, the world’s largest maker of semiconductors, Taiwan Semiconductor Manufacturing Company (TSMC), was forced to shut down production lines in response to a ransomware attack, and lost nearly US$86 million in 45 hours. In March 2019, one of the world’s largest aluminum producers, Hydro Norsk, became the target of a professional ransomware attack and lost around US$35 million in just one week.
With greater connectivity comes greater exposure to cyberthreats. The past decade has seen more cybersecurity incidents on operational technology (OT) and industrial control systems (ICSs) than ever before.
| Year |
Major ICS Security Incidents |
Attack Targets/Industry/Region |
| 2010 |
Stuxnet |
PLC (Nuclear Power Plant in Iran) |
| 2011 |
Duqu |
Computer/Server (Public Utility in Multiple Countries) |
| 2012 |
Disttrack/Shamoon |
Computer/Server (Oil Company in Saudi Arabia) |
| 2014 |
Sandworm |
SCADA/HMI (Factory Floor in Multiple Countries) |
| 2015 |
BlackEnergy/KillDisk |
HMI/Serial Device (Power Grid in Ukraine) |
| 2016 |
Industroyer |
Circuit Breaker (Power Substation in Ukraine) |
| 2017 |
Dragonfly |
Computer/Server (Public Utility in US/EU) |
| 2018 |
WannaCry |
Computer/Server (Factory Machines in Asia) |
| 2019 |
LockerGoga |
Computer/Server (Aluminum Producer in Norway) |
| 2019 |
DTrack |
Computer/Server (Nuclear Power plant in India) |
Table: Some major cyberincidents during the past decade1.
Battlefields
If we look closely at the targets of these attacks, two types of industries emerge: critical manufacturing and critical infrastructure.
Critical manufacturing includes large companies such as TSMC and Hydro Norsk, who both play an important role in the worldwide supply chain. The consequences of cyberattacks on critical manufacturing go far beyond the corporate profits for that organization. In fact, the global supply chain itself can be disrupted by just a click of a mouse or the tap of a key.
Critical infrastructure includes the utilities for an entire country’s energy, water, and transportation operations. If a nation’s infrastructure is shut down due to a cyberattack, there could be a devastating impact on human life and the environment. For example, a cyberattack on a Ukrainian power substation in 2016 left more than 200,000 people in the dark for up to six hours in the middle of winter.
Tackling the Problem on All Fronts
As OT/ICS networks are no longer isolated from cyberthreats, the next question is: how do we protect critical infrastructure and manufacturing systems from the growing threat of cyberattacks? Obviously there is no simple answer. Instead, the solution requires all stakeholders across the public and private sectors to make a long-term commitment to all aspects of cybersecurity.
We look at six ways the public and private sectors can protect industrial networks.
Public Sector Push
Governments around the world have become one of the major driving factors for improving cybersecurity in OT/ICS networks in recent years.
- In 2018, the United States government formed the Cybersecurity and Infrastructure Security Agency to coordinate efforts for protecting the nation’s critical infrastructure and essential resources2.
- In 2018, the state legislature of California passed a new law, SB-327, which requires IoT device manufacturers to provide proper security features to protect user privacy and the user’s data stored and collected on their devices3.
- In 2018, the European Commission passed the Cybersecurity Act to strengthen the ability of the EU Agency for Network and Information Security (ENISA)4.
- In 2019, the Chinese government released a new version of the Multi-level Protection Scheme, known as MLPS 2.0, which extends the regulatory scope of cybersecurity laws from traditional information systems to critical information systems, industrial control systems, and the Internet of Things.
Private Sector Drivers
Despite business competition, OT users and solution providers in the private sector have also formed various associations and alliances to develop more useful best practices for security.
- In 2019, the International Society of Automation (ISA) initiated the Global Cybersecurity Alliance (GCA) to discuss how to address cyberthreats amid the ongoing trend towards IT/OT convergence5.
- Also in 2019, the Operational Technology Cyber Security Alliance (OTCSA) was formed to provide comprehensive cybersecurity guidelines for operational technology. The members include OT operators, such as ABB and Wärtsilä, along with IT/OT solution providers, such as Check Point, Microsoft, and Qualys6.
Open Standards and Guidelines
Until recently, private sector solution providers have been coalescing around the IEC 62443 standards on security capabilities for control system components. The standards provide a flexible framework to address current and future cybersecurity vulnerabilities in industrial automation control systems.
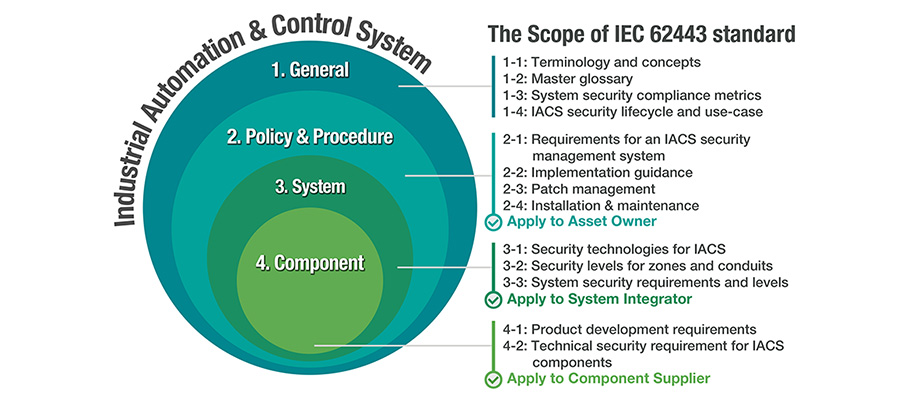
The Industrial Internet Consortium (IIC) also publishes the “Industrial Internet Security Framework (IISF) Report”, which brings together the collective wisdom of over 25 companies and academic institutions around the world to provide in-depth guidelines across various industries7.
Cybersecurity Is the Future of OT/ICS
As illustrated by the growing number of cybersecurity incidents involving critical infrastructure and manufacturing in recent years, a concerted effort is needed to ensure our safety now and in the future. After all, if we fail to address cybersecurity concerns for OT/ICS networks, no amount of AI or big data can help us achieve the full promise of digital transformation. Governments and private sector solution providers around the world have recognized the urgency of this issue and are working together to push the cybersecurity agenda throughout the entire OT/ICS industry. Ingraining cybersecurity into the DNA of OT/ICS entails more than adopting a new software application or machine on your industrial network. Cybersecurity needs to be embedded throughout every aspect of each organization.
To learn more about how forces from the government and private sectors can protect industrial networks, please download the white paper.
1 For more information, download the Moxa white paper: Industrial Network Cybersecurity: Debunking the Myths and Adopting Best Practices
2 https://www.us-cert.gov/about-us
3 https://leginfo.legislature.ca.gov/faces/billTextClient.xhtml?bill_id=201720180SB327
4 https://ec.europa.eu/digital-single-market/en/news/cybersecurity-act-strengthens-europescybersecurity
5 https://isaautomation.isa.org/cybersecurity-alliance/
6 https://otcsalliance.org/
7 https://www.iiconsortium.org/IISF.htm