Securing operational technology (OT) networks and increasing network durability are key to enhancing operational resilience, as OT network protection still lags behind information technology (IT) cybersecurity. This article explains the reasons behind the lag, how this gap manifests across different industries, and outlines four steps OT operators can take to better protect OT networks from cyberattacks and enhance operational resilience.
New Opportunities Bring New Threats
As new IT technologies and Internet connectivity become available to OT networks, many different opportunities are opened up for greater productivity and efficiency. Although connecting OT networks to the Internet enables new possibilities, it also introduces new threats.
With more people working remotely due to the COVID-19 pandemic, companies need to enable more remote connections to their business and production networks. Although these remote connections do enable employees to work from the safety of their homes, they also unfortunately open the gate to new cyberthreats.
Although IT networks are usually safeguarded with sophisticated cybersecurity countermeasures, OT networks still include many legacy devices and often have less protection. This is primarily because the systems are complex and it is quite difficult to effectively implement cybersecurity measures. In addition, these networks often have long lifecycles, where legacy devices are not regularly updated with cybersecurity features. In fact, OT protocols are not usually encrypted and often lack authentication mechanisms. Moreover, hackers are becoming more familiar with OT protocols, networks, and devices, enabling them to target PLCs, HMIs, and SCADA systems more easily.
The Cybersecurity Gap Between IT and OT
The reason for the discrepancy between the maturity of IT and OT cybersecurity is closely related to different business priorities that often conflict with each other.
- Why IT networks are better protected
Enterprise IT networks prioritize confidentiality and focus on data integrity. IT assets include computers and servers located in climate-controlled office environments, and are fairly easy to upgrade, patch, or replace on a regular basis.
- Why OT networks lag behind
Industrial OT networks, however, prioritize availability and focus on controlling processes that cannot tolerate downtime. Unlike IT assets, OT networks are made up of PLCs, HMIs, meters, and other pieces of equipment that are difficult to upgrade or patch. These devices can be located in harsh environments that are difficult to reach and are often subject to extreme temperatures, vibrations, and shocks.
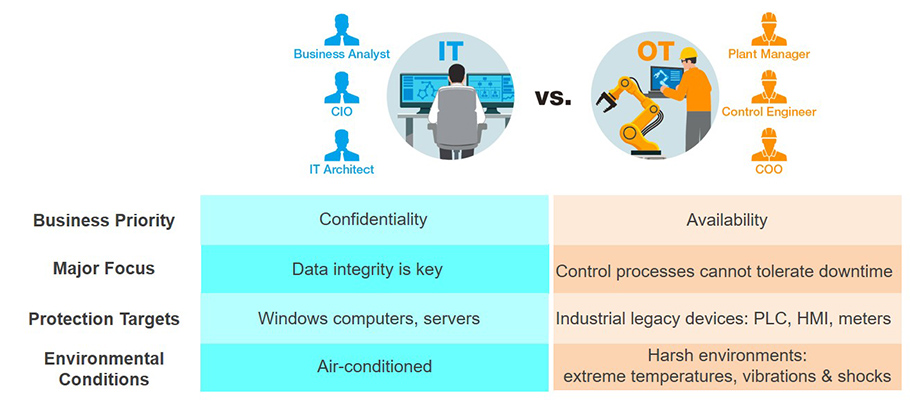
Table: IT and OT Cybersecurity Gap
Different Demands in Different Domains
Industrial applications have different requirements that differ depending upon the sector, as well as varying levels of cybersecurity maturity. Although industries in the public sector are generally better protected than private manufacturing businesses, the vast majority of OT networks still lag behind their IT counterparts in terms of cybersecurity. In general, IT departments administer the cybersecurity policies for OT networks, but those policies are merely at the IT level, which means they do not take into consideration the characteristics and requirements of OT networks. In addition, many also continue to lack segmentation between their IT and OT networks. Regardless of the industry, many OT networks lack sufficient security controls and are not managed by OT operators.
Factory Automation
Manufacturers generally have lower levels of cybersecurity maturity and are primarily revenue driven and focused on maintaining availability and uptime rather than on security. Even though the level of security awareness varies depending on whether the manufacturer is traditional, transforming, or modernized, IT and OT roles and responsibilities continue to be vaguely defined in factory automation.
|
Types of Factories
|
Traditional Factories
|
Transforming Factories
|
Modernized Factories
|
|
Status
|
- Full of legacy systems
- Lack of network architecture
- Lack of security awareness and resources
|
- Mixture of new and legacy systems
- Complex network environments
- Wider attack surface
- Have security awareness but it might not be a priority
|
- High automation and cybersecurity maturity
- Assigned cybersecurity resources
- Integration with SOC
- Holistic cybersecurity
|
|
Concern
|
Cybersecurity is not a priority and they do not have sufficient protection
|
Managing both legacy and new networks at the same time
|
Preventing operational disruptions with cybersecurity measures deployed
|
Table: Different Types of Factories and Their Concerns
Power Utilities
Cybersecurity for power grid applications is mostly driven by government policy. However, dedicated OT networks for power automation have low visibility of network assets, limited protection, and are in the process of transformation from RTU to Ethernet technologies. These applications are primarily concerned with passing government audits and meeting international standards (IEC 61850, IEC 62351, IEC 62443, and ISO 27001), preventing misconfigurations from operators, and preventing disruptions to power distribution.
Water Treatment
Similarly, water treatment applications are comprised of dedicated OT networks that have low visibility of their assets. The abundance of legacy devices as well as a lack of access control and network segmentation indicate a need for strengthening cybersecurity beyond government audits and deploying firewalls and intrusion prevention systems (IPS).
Intelligent Transportation Systems
Cybersecurity in Intelligent Transportation Systems (ITS) is also primarily government-driven. ITS applications are characterized by distributed networks with various devices and systems at each traffic intersection. Although each device often uses a different network, security is centralized at the IT level.
Although ITS applications follow prescribed government guidelines and are pretty good at establishing cybersecurity policies and deploying firewalls, they are still concerned about cyberattacks on traffic signals and sensors, as well as the possibility that someone could break in to an equipment cabin relatively easily and gain direct access to the network that way.
Four Steps to Enhancing Operational Resilience
Considering how different IT and OT networks are, how can we bridge the gap between these two domains and secure OT networks from cyberattacks? To enhance operational resilience, OT networks have to ensure their cybersecurity measures are as mature as those utilized in IT networks. The following four steps describe how you can secure your OT networks and increase resilience.
1. Manage Your OT Networks
You cannot protect the assets you do not know you have. That’s why the first step to enhancing operation resilience requires OT operators to monitor everything on their networks in a similar way to how IT network administrators often have complete visibility. Is everything that should be on your OT network actually there? Is there anything on your network that should not be there?
For example, OT operators can start to determine who can and cannot access the network by leveraging ACL or other authentication mechanisms. Furthermore, there are simple mechanisms that OT operators can set up to define which PLC can be connected to the network by port access control or sticky MAC. In other words, everything on the trusted list is allowed to go through the network, and anything not specified on the trusted list is blocked. Managing your OT network (instead of relying on the IT department) also allows OT operators to respond more quickly to downtime and troubleshoot issues more rapidly.
2. Segment Your OT Networks
Unlike IT networks that can be segmented by dividing the network into different departments with their own set of permissions, OT networks are essentially one giant Intranet where everything is connected. This makes OT networks more difficult to segment, but not impossible. There are two ways you can segment an OT network:
- Vertical segmentation involves adding an Industrial Demilitarized Zone (IDMZ) between the IT network and OT network. Although this separation should be mandatory, many companies still have not segmented their OT networks from their IT networks.
- Horizontal or lateral segmentation involves creating and separating cells, zones, and sites on the OT network. A cell is essentially a tiny place where all equipment is stored, such as a cabinet. Several cells can form a zone, and multiple zones can form a site.
Segmenting OT networks using either method, or both, allows operators to prevent cyberthreats from spreading to other parts of the network.
3. Patch Vulnerabilities
Since equipment and devices running on OT networks cannot be upgraded or replaced as frequently as endpoints on IT networks, OT networks still have many legacy devices that may even be running on operating systems as old as Windows 95. Many legacy OT devices remain unpatched and are relatively easy for hackers to exploit. If no patch is available from the original equipment vendor, consider putting a virtual patch on a device that goes in front of your legacy devices.
4. Secure Remote Connections
Protecting the data that is transmitted from your plant or remote site back to the monitoring and control center is absolutely crucial. Ensure that each remote connection to your OT network is both authenticated and encrypted. Authentication verifies the identity of the user requesting access whereas encryption ensures that the data transmitted is securely encoded and cannot be easily deciphered by prying eyes.
Summary
Besides managing and segmenting OT networks, OT operators also need to ensure their systems are properly patched and remote connections are secure. These steps not only help reduce the gap between OT and IT departments, but also protect industrial control systems, which are increasingly being connected to the Internet, from cyberattacks. To learn more about how to build secure network infrastructure, please visit our microsite: https://www.moxa.com/en/spotlight/portfolio/industrial-network-security/secure-network-infrastructure.htm