The main benefit of an industrial automation control system (IACS) is that it facilitates greater efficiency through remote management, the ability to converge multiple networks, and the automation of network processes. However, the vulnerability of IACS networks increases as more devices and networks require access, which is common within the Industrial Internet of Things (IIoT). It is crucial that system operators do not sacrifice the security of the network when reaping the benefits of IACS networks. For example, when networks converge, someone with malicious intent who has gained access to a single device on the network can easily control and corrupt other areas and devices on the network.
Although the risk of a security breach on IACS networks can never be completely eliminated, system operators must follow best practices in order to minimize this risk. This article will now briefly consider three aspects that many cybersecurity experts believe system operators need to address in order to ramp up the security of IACS networks.
Three Factors that Help Ramp Up the Security of Industrial Networks
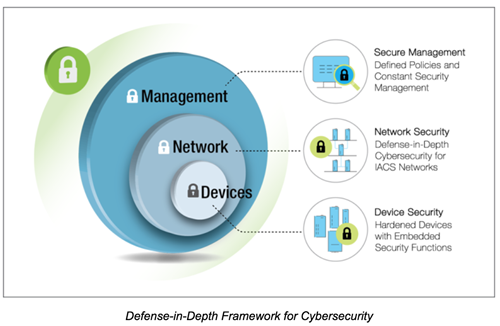
Device Security
The first issue that needs to be considered is device authentication and access protection. The second concern is how to utilize an easy-to-use and effective password policy as system operators will have hundreds of devices installed on their industrial network. Finally, the system operator needs to know how to ensure that all network devices have the ability to collect and store event logs. The reason why event logs are important is because they alert the system operator to what happened on the network and why it happened, which will allow them to fix the problem as quickly as possible.
Network Security
System operators need to decide which devices or systems need to have the highest levels of protection. In addition to this, they also need to understand the defense-in-depth approach and why it should be utilized in order to ensure that the network remains secure. Finally, the challenge of how to ensure secure remote access through the use of firewalls and VPNs must also be considered.
Secure Management
It is essential that system operators understand the recommended procedures for security policies and guidelines developed by experts in order to ensure that the network is protected throughout the entire network lifecycle. In addition, they need to know how to manage the security of the entire network and how to simplify the configuration and management of security settings. When security settings are too complicated, as is often the case on industrial networks, system operators will tend to ignore recommended guidelines and not implement security settings.
How to Implement a Secure Industrial Network
The section below will give system operators a step by step overview of the three aspects that need to be considered in order to implement a defense-in-depth security architecture.
Defense-in-Depth Security Architecture
Step 1: Network segmentation
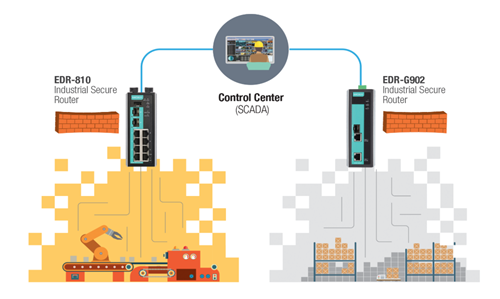
Network segmentation involves breaking down the network into physical or logical zones with similar security requirements.
Step 2: Define zone-to-zone interactions in order to scrutinize and filter network traffic.
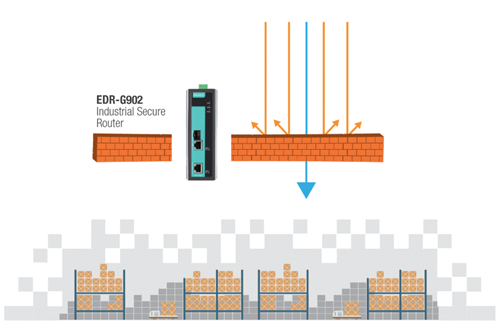
In order to enhance network security, the traffic that passes between zones in the IACS must be scrutinized and filtered.
Step 3: Support secure remote access on industrial networks.
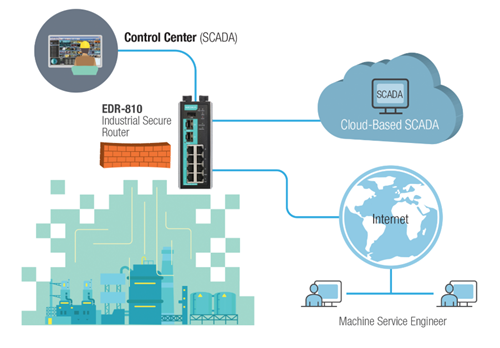
For networks that require the remote site to be constantly connected to the IACS, it is advised to use a VPN that supports a secure encryption method such as IPsec, which prevents unauthorized users from accessing the network.
Secure Industrial Network Devices
It is strongly advised to deploy network devices with good cybersecurity. This will ensure that devices cannot have their settings altered by a person that wants to put the devices or the network at risk. Many cybersecurity experts view the IEC 62443 standard as the most relevant publication for how to secure devices on industrial networks.
Secure Monitoring and Management
After determining that network devices and the network topology are secure, a network management policy needs to be established to ensure that the network remains secure throughout the entire network lifecycle. In order to achieve this, system operators should have a series of guidelines to follow. This will allow them to implement procedures that follow best practices to ensure that secure monitoring and management of the network takes place as smoothly and reliably as possible.
To learn more about what has to be achieved in order to build, manage, and maintain secure IACS networks, please download the white paper: Three Aspects to Consider in Order to Secure Industrial Automation Control System.