With connectivity increasing in industrial environments, every device that is added to a network creates a potential weak point or vulnerability on industrial networks or industrial control systems. This evolution of networks is forcing asset owners to consider how to enhance their security status to mitigate risks that can compromise the operational availability of their systems. Most network operators agree that the best method to protect the security of their network is to follow the guidelines that are set out in the IEC 62443 standard.
Understanding the Security Risks
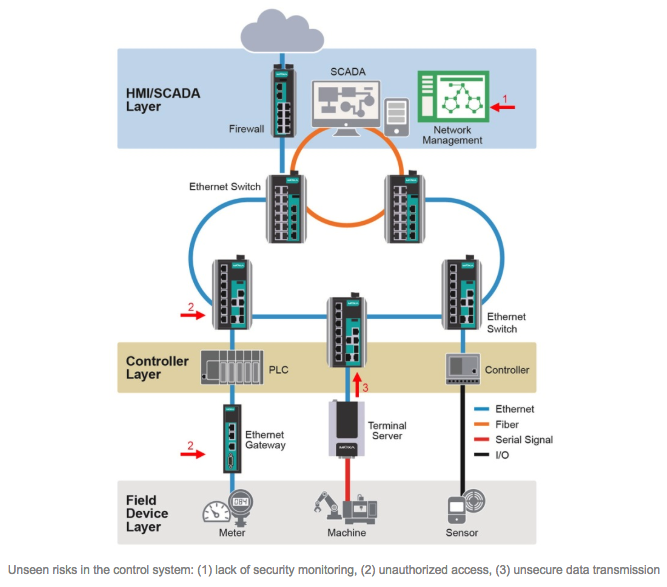
Among security experts, the general consensus is that the six main security threats to internal networks are: (1) unauthorized access, (2) unsecure data transmission, (3) unencrypted key data, (4) incomplete event logs, (5) lack of security monitoring, and (6) human configuration error. It is paramount that network operators understand these threats so that they can deploy devices that have sufficient security features in place and ensure that their networks are safe from internal and external threats. Consideration will now be given to situations where these security risks can arise and some of the options that are available to network operators in order to neutralize threats to their networks.
Prevent Intrusions and Attacks
Account management and password authentication are essential to secure the network. Moreover, an identifier management policy is also important and it will often include several parameters to further enhance the security of the network. These parameters will typically ensure that the accounts can only be used by the users they were created for, and that the users only have access to parts of the network that are required for them to fulfill their job roles. The devices deployed on the network should be capable of logging users out of accounts that they shouldn’t have access to and alerting the network operator of any violations. This will further reduce the chances of someone gaining unauthorized access to the network or devices.
Protect Sensitive Data
All devices on the network must support and enforce data encryption when data is transmitted on the network. This will almost eliminate the risk of data being stolen during transmission. The reason why data integrity is so important is because it guarantees that data is accurate, and that the data can be processed and retrieved reliably and securely when it is needed. Furthermore, the configuration of network devices in industrial control networks is highly important. If the configuration data is inaccurate, or is corruptible, it can cripple network operations. In order to reduce the risk of the configuration data being corrupted, it is essential for devices to support and enforce configuration encryption.
Visualize the Security Status of the Network
Software that visualizes the security status of the network allows network operators to monitor any abnormal or potentially damaging activity that is taking place on the network. In addition, this type of software can help network operators prevent problems before they arise by allowing network operators to see with a quick glance if the correct settings are applied to each device on the network. If a device isn't as secure as it should be, the network operator can identify the problem before a hacker has the opportunity to attack the device. The security features that are typically covered can include password policies, encryption, login credentials, as well as ensuring the integrity of the data.
Moxa's Solutions
Moxa, along with many other security experts in the industrial automation industry, strongly believe that the best way to protect the overall security of networks is to start with ensuring the security of the switches as well as the serial-to-Ethernet solutions. For more tips and information about Moxa's solution that helps asset owners mitigate the security risks on industrial networks, please download the white paper.